Teaching Houston Methodist to phish. You play a key role in protecting our precious data.
October is Cybersecurity Awareness month. It also marks more than two years since we started sending out phishing drills. These planned drills put you to the test by showing how equipped we are at recognizing suspicious emails.
Because email is the number one way cybercriminals can attack us, these drills are critical. The data continues to tell us this is a vulnerability, and we need this ongoing training. When it comes to protecting our precious patient and HM data, we all play a role — to be vigilant and careful with suspicious emails and report them.
Keeping it reel.
Just like fire drills are part of our emergency preparation, so are phishing drills.

The results from our very first phishing drill in September 2020 showed that we had a lot of room for improvement — with 27% of our employees clicking the link. For reference, large health care organizations average a 45% click rate in their first phishing drill, 17% after some initial training and are at 6% after a year of training.
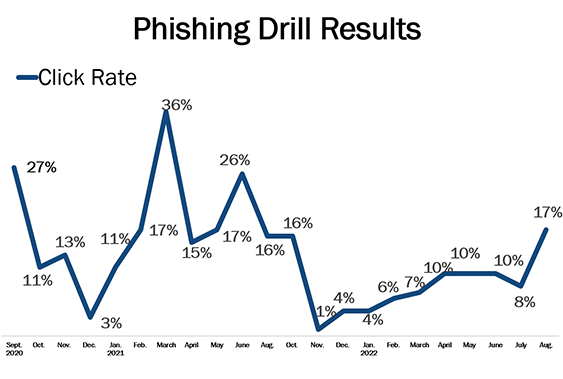
We’ve made a lot of progress since 2020. For the past year, we’ve averaged a 9% click rate. Cybercriminals are getting smarter, and we need to stay alert and continue training.
Improve your phishing skills.
To ensure systemwide awareness, HM Business Practices – Privacy and Information Security was recently added as a topic to our focal point review in-services. Other security features have been put in place to help us keep our data secure.
An [External] header is now visible in all emails coming from outside HM. This makes it easier for you to recognize a potentially suspicious email. We’ve also added more ways for you to report suspicious emails. All emails from external senders include a Report Suspicious button in the header. If you don’t know the sender and the email is suspicious, simply click the button to alert IT security. If you’re ever unsure, play it safe and report it. Taking that one, easy step to report a suspicious email could help HM catch a phish before someone else mistakenly clicks a malicious link.
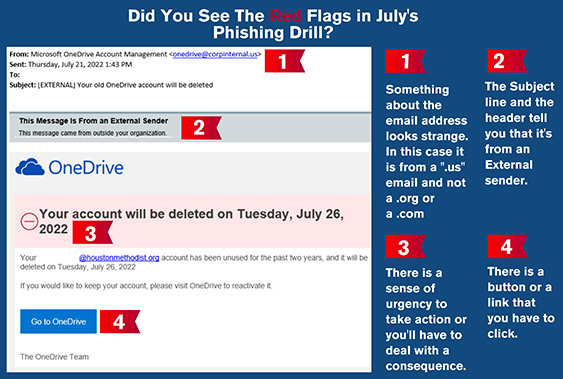
To help you understand what to look for, let’s break down one of our more recent phishing drills from July 25. Eight percent of you clicked the suspicious link. Here are the red flags that should’ve alerted you to why it wasn’t a legitimate email.
There’s something phishy.
With improved features to make it easier for you to report phish and ongoing training and communications to prepare you, we increase our ability to continue to keep our patient and employee data safe. Here are a few more helpful tips:
- Be careful what you click. Never open an attachment or click a link unless you know the sender.
- Check the address bar in your web browser. Any website that requires a form of payment will have a padlock icon to the left of the name. Never enter any payment information or personal data on a website that doesn’t have the padlock icon.
- Use two-factor authentication whenever possible. This is an extra layer of security to verify your identity.
- As the old adage says, “If it sounds too good to be true, it probably is.” Don’t click in emails or content when your gut is telling you that something doesn’t feel right.
For additional IT security tips, read the CIO Quarterly Report article: Data Security @ Home and Work. For more information on phishing drills by industry, view this 2022 report from knowbe4.com.
