Together, we block more than 1 million cyberattacks a day.
A million in one single day. That’s the number of cyberattacks that try to make it into our Houston Methodist email inboxes on a daily basis. One attack has the potential to seize patient data and paralyze an organization.
Globally, cyberattacks continue to trend upward. We have all seen it in the news. Thankfully, we have measures in place to protect our patients and HM data. Plus, we are in this together. You play a key role in staying alert and reporting any suspicious emails. When it comes to cybersecurity, we all play a part in keeping our patient and employee data secure.
How you can help keep us safe.
One of the easiest and best ways you can help protect our patient and employee data is by reporting suspicious emails.

We’ve made this process even easier by adding a Report Suspicious button right in the header of all emails sent from someone outside of HM (also referred to as an external sender). By clicking the Report Suspicious button, you’re alerting HM IT to review the email. If it’s found to be malicious, it will be automatically deleted from all inboxes systemwide. Your quick action can help prevent a cyberattack.
When you report an email as suspicious, you will receive a follow-up email confirming if it is actually safe or not. The email will also let you know your next steps. For example, if the email was marked as safe, but you don’t want emails from this sender, you’ll get instructions on how to proactively block and remove these emails from your inbox permanently.
Taking a deeper dive. Can you recognize a phish?
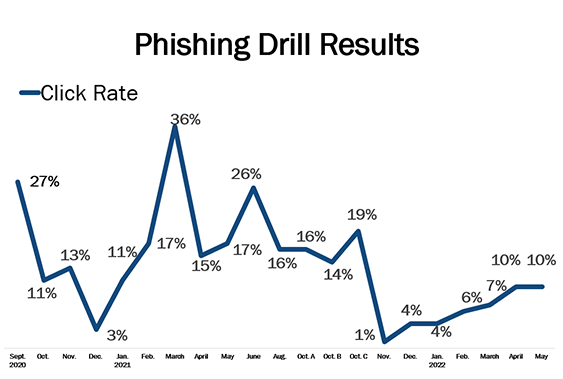
As part of our continued commitment to keeping our patient and employee data safe, IT has been conducting phishing drills since September 2020. These drills test our ability to recognize a real phish and track our reporting of suspicious emails.
Overall, while we’re getting better at catching phish, we still need more practice. The graph below illustrates the percentage of HM employees who’ve clicked a link or an attachment from a planned phishing drill. Note: Opening an email is OK. It’s the act of clicking a link or opening an attachment that can cause damage. In a real cyberattack, clicking is what would likely be the culprit of a hacker accessing sensitive information.
One phish. Two phish. Three phish. Phishing, vishing and smishing.
It may sound like the title of a Dr. Seuss book, but phishing, vishing and smishing are anything but child’s play. They’re three types of cyberattacks and some of the most common threats impacting organizations globally.
Phishing.
A phish is a type of cyberattack but, generally speaking, it refers to an email scam. A phish usually has four characteristics:
- Sent from someone you don’t know.
- Email or site name may be tweaked to appear as though it’s from a trusted sender.
- Has an urgent tone and is asking you to click a link or open an attachment.
- Often includes an offer that sounds too good to be true.
All suspicious emails should be reported. Even though our cybersecurity team has advanced systems in place and is able to block the majority of phish, your actions serve as an extra layer that can help prevent a cyberattack.
Vishing.
Vishing is short for voice phishing and typically involves phone fraud (often from an automated system). The classic case usually starts with the caller stating they’re from your bank or credit card company and that your data appears to have been compromised. In other words, they’re calling to help you because you’ve been victimized.
To “help you,” the caller needs you to verify your information. Since this sounds personal and urgent, you may be eager to share your information. If you do, the hacker has now gained your sensitive information. If you get one of these calls, hang up and contact your bank or credit card company to confirm that they are trying to reach you and alert them of this suspicious activity.
Smishing.
Increasing in popularity is the use of smishing, short for “text message phishing.” This name comes from the technical term Short Message Service or SMS. These are usually easy to spot as the sender doesn’t register as a known number in your smart phone and the message requires you to take urgent action by clicking a link.

If you ever get a suspicious text message, you can report it to your cell service provider by forwarding the text to 7726 (SPAM). Your provider will respond with a text message asking for the sender’s number or email (in rare cases the texts comes from an email). The best practice is to never click any links in a text message when you’re not familiar with the sender. For instructions on how to forward a text message, view this article from AT&T.
Don’t get hooked.
Some of these cyberattack strategies or their fancy names may be new to you, but the common thread among them all is simple. Whether it’s an email, a call or a text – if you don’t know the sender, always question it. Don’t click any links or attachments, and never share personal information. Cyberattackers aren’t going away, but together we can help block them from entering HM.
HM Chief Information Security Officer Barry Beckett said it best when he shared the following message:
“Everyone can help defend Houston Methodist by focusing on three cybersecurity fundamentals.
- Keep all your work and personal devices updated and running on the most current software.
- Use two-factor authentication for personal and work access.
- Use the Report Suspicious button to report suspicious email.”

