Fostering a Culture of Security
We see it every day in the news about companies getting hacked. Safeguarding our patient data and corporate systems is a collective effort that requires keen attention to detail and willingness from each of us to do our part. “No matter how prepared we are today, we’re always working to get better tomorrow, because cyberattackers are getting better, too,” said Barry Beckett, director of security and chief information security officer. “When it comes to cybersecurity at Houston Methodist, we need everyone’s support. We’re in this together — it’s everyone’s business and everyone’s job.”
Here are a few ways you can help foster a culture of security and protect our precious patient data.
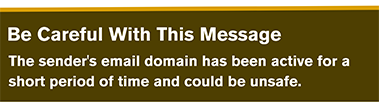
Be careful…looks can be deceiving
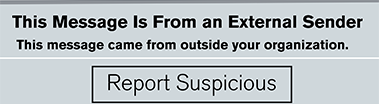
Cybercriminals are becoming more sophisticated by registering new look-alike domains from which to send phishing messages (e.g., something like houstonmethod1st.org). To help make you aware of these potential suspicious emails, a Be Careful banner appears when you receive an email from an external sender whose domain is less than 90 days old. If you have any doubt about the validity of an email’s sender, be sure to click the Report Suspicious button in the top right corner of Outlook and IT will investigate it for you.

Make mine multifactor
Multifactor authentication (MFA) protects your personal information by creating an added layer of security to your accounts. It prevents someone from logging in even if they have or figure out your password. This additional measure uses something you know (password) as well as something you have (access to your phone’s text messages). This allows HM to securely verify your identity when accessing our systems. It’s also an important safety measure to use for all your personal accounts (e.g., Google, social media, bank accounts, etc.) because it can stop hackers from getting in. Visit your accounts’ websites for instructions on how to set up MFA. They’re often found under the settings or security tab, and it’s quick and easy to do.
For an added layer of security and peace of mind, if you have a second phone number, add it to your Microsoft Sign-In System account. The second number serves as an alternative if you misplace your mobile device or want to change your primary mobile phone number. This applies whether you have an HM-provided mobile device or not. You can add a personal mobile, desk work phone, home phone, etc. To verify that you have two phone numbers, or to change or delete numbers, click this link.
You can also have the code you receive sent to an app. Simply install the Microsoft Authenticator app, which allows you to validate your identity through the app instead of receiving the code via text or phone call. This is especially helpful when you need to access HM resources but can’t receive calls or texts, such as when you’re on an airplane and you can have the code sent to multiple devices, not just your mobile device — to install/set up the Microsoft Authenticator app, follow these instructions.

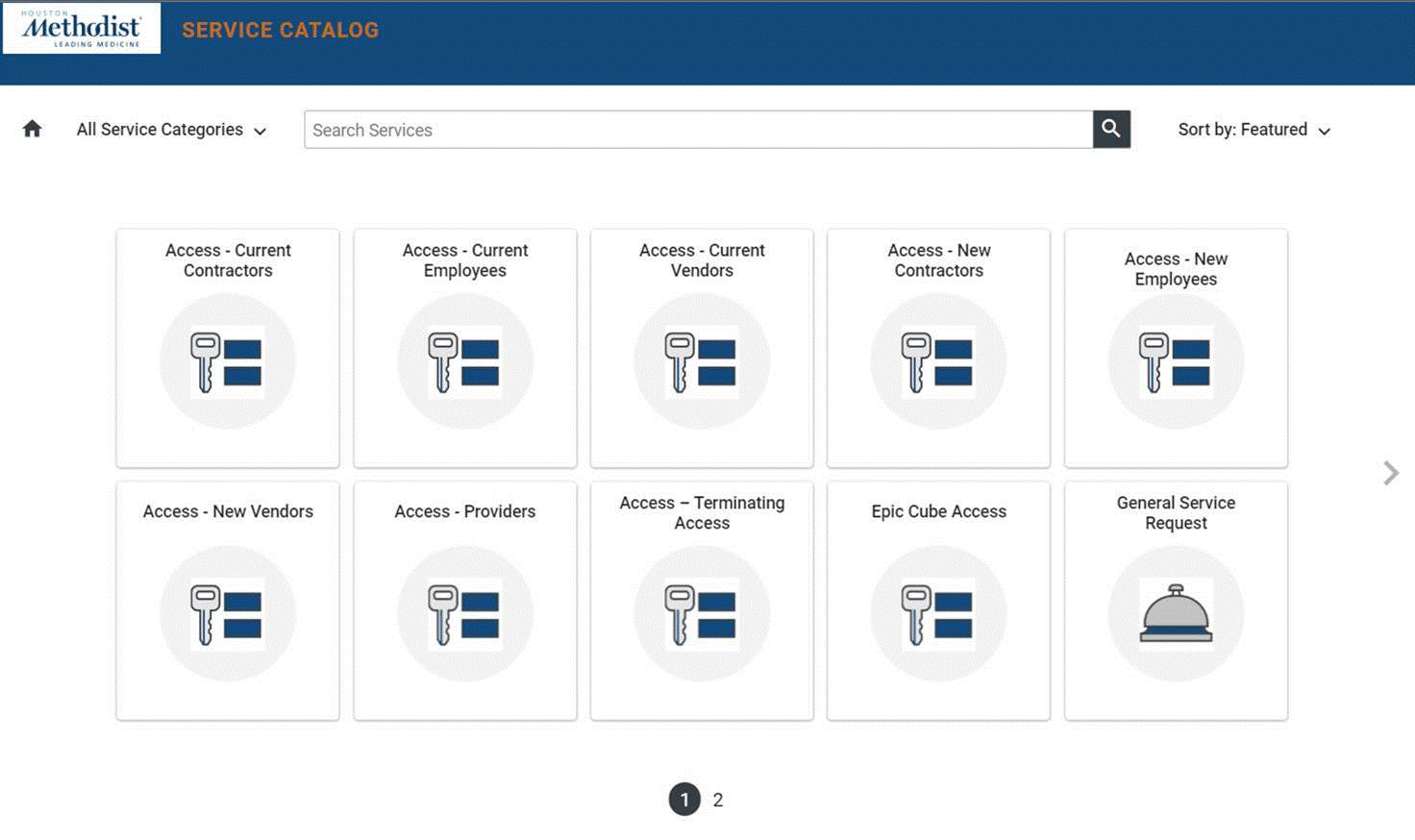
Submit System Access Requests online
To make it easier for you and to stay secure, all System Access Request forms now must be submitted electronically on the IT Support website (itsupport.houstonmethodist.org) using an automated form. This makes it convenient for you to submit and track your requests. PDF forms are no longer accepted, which increases security. Policy IM24 has been updated to reflect these changes.
From the website click the Request Service button at the top or under the Forms & Resources section. Click IT System Access Request Forms to be taken to the Service Catalog, where you can choose the appropriate form for your needs. For example:
- New employees, contractors or vendors – must be submitted by the hiring manager, HR or executive assistant.
- Current employees, contractors or vendors – can be submitted by the user but must include manager approval attached to the ticket. You would primarily use this for access to VPN, OneDrive, SharePoint, etc.
- Terminating users – a new form specifically for terminating user access is now available. This must be submitted by the hiring manager, HR delegate or an executive assistant. This would be primarily used for contractors and vendors. Note: When an employee leaves, once you terminate the employee in MARS, it will automatically remove the employee from the system each night. Unless the termination requires urgent removal, you don’t need to alert the IT Service Desk.
How you can help
Creating as many security layers as possible to keep cybercriminals out is something we take seriously in IT, but you can help, too. Hacking email is the most common way cybercriminals use to break through an organization’s cybersecurity system. Stay vigilant and alert. Be sure to foster that culture of security by reporting suspicious emails, using MFA and securely submitting your service requests.
